Linux distribution for embedded applicationsOpenWrtIt has been revealed that there was a vulnerability in the update system of “ that could cause a malicious package to be mistaken for a genuine package.” It seems that hash generation using SHA-256 was improperly implemented, making it easy to cause hash collisions.
Compromising OpenWrt Supply Chain via Truncated SHA-256 Collision and Command Injection – Flatt Security Research
https://flatt.tech/research/posts/compromising-openwrt-supply-chain-sha256-collision/
Attended Sysupgrade Server CVE-2024-54143
http://lists.openwrt.org/pipermail/openwrt-announce/2024-December/000061.html
OpenWrt allows you to update firmware from the router settings screen with just a few clicks.Attended SysupgradeIt has a system called “. This Attended Sysupgrade has a mechanism that “builds a firmware image on the server side based on the user’s device information and desired version, and sends it to the router”, but it is said to have a “vulnerability that allows arbitrary commands to be executed”. It has been discovered that there is a vulnerability that allows a malicious file to be mistaken for a genuine file through a hash collision attack.
The security researcher who discovered the problemRyotaKAccording to him, Attended Sysupgrade was validating packages using only 12 digits of the 64-digit hash value generated by SHA-256. This made it very easy to perform a collision attack where a portion of the malicious file was rewritten to generate the same hash value as the genuine package.
Mr. RyotaK tried a collision attack using GeForce RTX 4090 and succeeded in colliding hash values within an hour. By combining this collision attack with a command injection attack that was discovered separately, it was demonstrated that it is possible to “mistake a malicious package as a genuine package and install it into the user’s router via Attended Sysupgrade”.
Mr. RyotaK has already reported the vulnerability to the OpenWrt development team, and the development team applied the fix and started the Attended Sysupgrade service within three hours of the report. Details of the vulnerability and countermeasures are summarized in the link below.
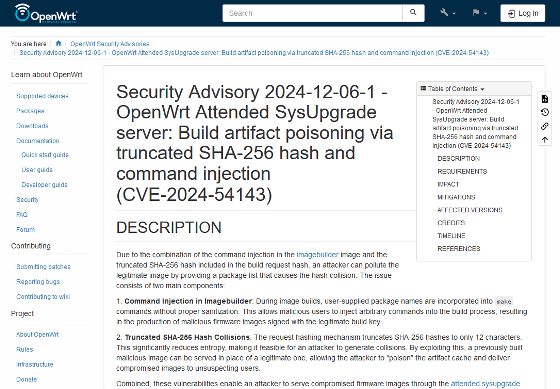
[OpenWrt Wiki] Security Advisory 2024-12-06-1 – OpenWrt Attended SysUpgrade server: Build artifact poisoning via truncated SHA-256 hash and command injection (CVE-2024-54143)
https://openwrt.org/advisory/2024-12-06
Copy the title and URL of this article
・Related articles
Google succeeded in breaking the hash function “SHA-1” and plans to release the method in 90 days – GIGAZINE
Summary of basic knowledge of “post-quantum cryptography” that the general public should know for the coming era of quantum computers – GIGAZINE
Chinese researchers build a method to decipher RSA encryption using quantum computers – GIGAZINE
Google announces quantum chip “Willow” that can perform calculations that would take 10 to the 25th power years on a supercomputer in just 5 minutes – GIGAZINE
Official Wi-Fi router “OpenWrt One” with pre-installed OS “OpenWrt” for embedded devices finally released – GIGAZINE